August 18th, 2025
v1.4.0: Credential Monitoring (beta), Cloud context, Rate Limit, and many improvements
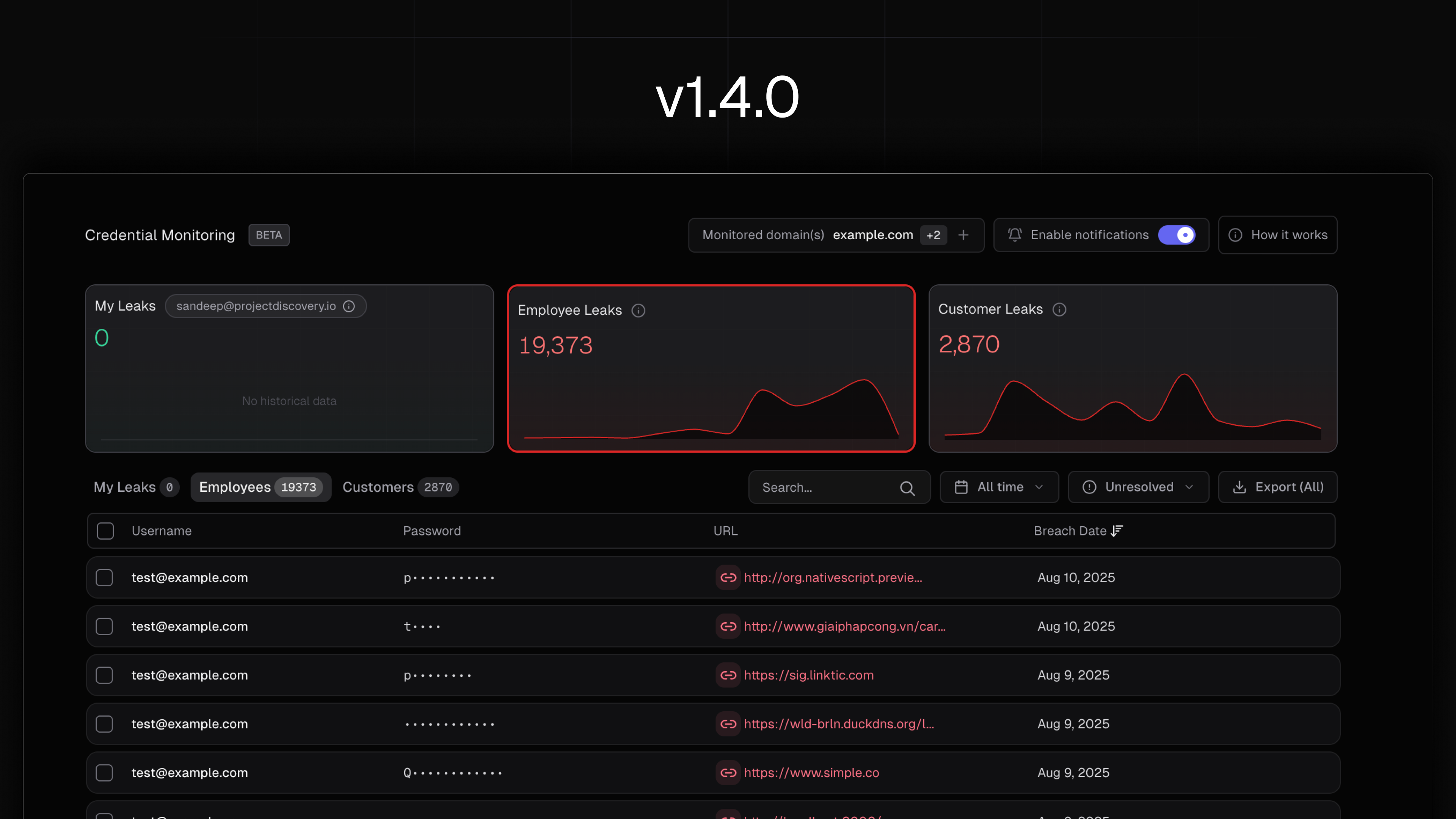
Credential Monitoring (beta)
A new Leaks experience continuously surfaces exposed credentials associated with your organization so you can spot account-takeover risk early and act before attackers do. Access is scoped by role to protect sensitive breach data, and organization-wide visibility unlocks after domain verification. Enterprise teams can manage multiple domains and integrate via API.
Learn more here:
https://docs.projectdiscovery.io/cloud/credential-monitoring
Rate Limit per Host
A new scan configuration option enables control over request rates to safeguard host stability and optimize resource usage. Use the “Rate limit per host” setting to define requests per second per host, leave blank to default to maximum scan speed. Lower values enhance host respect, while higher values boost throughput. This control is scoped within scan configurations and integrates seamlessly with custom headers, variables, and enterprise-grade features like fixed IPs and whitelisting to ensure predictable, compliant scanning behavior.
Learn more here:
https://docs.projectdiscovery.io/cloud/scanning/parameters#rate-limiting
Contextual Metadata for Cloud Assets
Asset drawers now include enriched metadata from connected cloud providers to help you understand what you’re looking at without switching tools. For example, an AWS S3 bucket or a Kubernetes ingress will display the key integration details you typically hunt for, things like the instance identity, how traffic reaches it, the control plane objects it’s tied to, and the versioning and ownership breadcrumbs that matter during triage. The goal is simple: when you pull up an asset, you immediately see the operational shape around it so you can make a confident call on severity and next steps. Filtering on these metadata fields is coming soon.
Asset Source Visibility
The asset drawer now includes source details, making it easier to see where discovered assets originate and providing context for external discovery. This lives under the Asset → Drawer details panel.
WAF statistics in scan logs
Scan logs now include a WAF-focused summary to make it easier to see when scans are being challenged or blocked and to guide tuning (e.g., white-listing, throttling or header strategies). This lives under the Scan → Logs details panel.
UI & UX Improvements
Prevented recommended profiles from being auto-selected multiple times in the template option workflow.
Fixed scan button behavior in grouped asset view, ensuring scans can be initiated correctly.
Introduced a new score progress bar for clearer visibility of Security Score improvements.
Enhanced the timepicker with smoother UX and resolved edge-case bugs in time selection.
Improved loading state on the Teams page to provide clearer feedback during team invites.
Resolved template handling in the scan dialog, fixing issues with running custom and GitHub templates.
Stability & Performance
Eliminated a race condition in port-scan result callbacks that could trigger occasional panics.
Refined per-worker rate-limit calculations to prevent host skipping.
Added additional panic guards across components (including headless and technology-detection paths) for broader coverage.
Improved scan worker calculation logic for more predictable scheduling under variable load. Fixed an edge case with the retest vulnerability option.
Added a fallback path when a scan configuration isn’t found, reducing hard failures.